Slack is one of the most commonly used apps on the Internet.
So of course it will be used by hackers.
And while we continue to monitor an uptick in Slack-based attacks, we're also noticing hackers using Slack for other attacks. 
The Attack: Avanan researchers discovered a new attack that uses a Slack redirect to bypass Microsoft SafeLinks. It looks this:
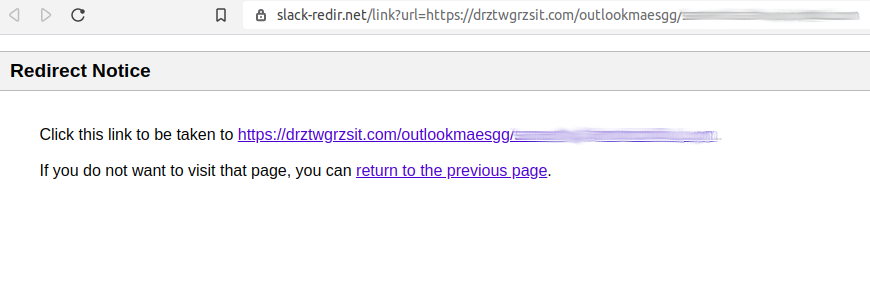
You can see the beginning of the URL at the top: "slack-redir.net"
This was able to bypass SafeLinks and bring the user to a fake Microsoft login page that would steal their credentials.
Simple enough. But here's what's odd.
The Open Redirect vulnerability was first discovered in February 2019.
Leaving that vulnerability open, and deciding not to fix it, could, in my view, be the wrong call. Regardless of the business rivalry forming between Teams and Slack, Slack should make sure its platform is not leveraged by hackers for any attacks, even when against a competitor.
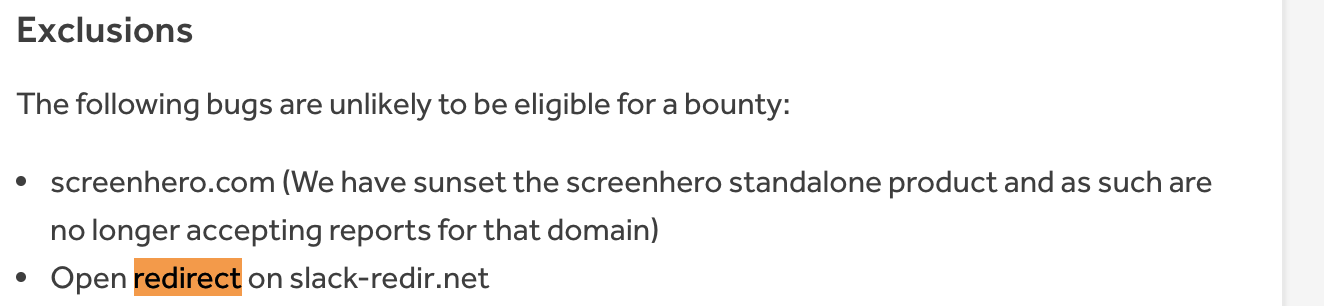
Why it Matters: Open redirects are common. And this particular redirect is not new.
What is new is that a widely reported redirect is getting past SafeLinks.
Hackers inserted a function in the code to ignore the Slack redirect URL split, and have SafeLinks analyze only after the redirection.
So let's recap:
- This vulnerability that allows hackers to use its redirect to steal credentials from unsuspecting users has been known for years.
- Microsoft SafeLinks is being fooled by a simple phishing redirect email that is widely known and can be easily stopped.
It's why you need robust, defense-in-depth protection. With Avanan, you have protection that buffets Microsoft ATP, including SafeLinks. And Avanan has protection for Slack.
Avanan is often a better choice—we have the granularity to secure everything.








