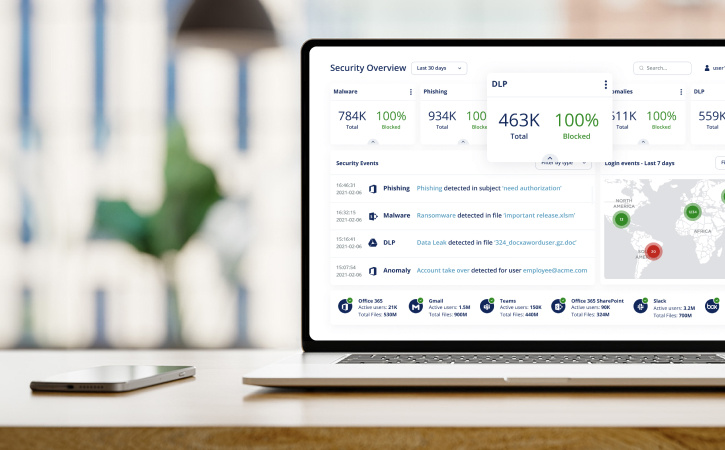
Excellent visibility and control of sensitive data flowing in and out of your organization.
Check Point's SmartDLP offers a structured approach to data loss across your enterprise, from email to collaboration.

Check Point leverages the industry's most advanced tools to identify and mark files containing confidential, financial, and personally identifiable information, including credit card numbers, social security numbers, and bank routing numbers. When necessary, Check Point adds a -classified suffix to the end of confidential messages or files.
Flexible workflows determine if the content is quarantined, the user is alerted, and/or the file is encrypted with IRM.

Check Point uses cloud-native controls to enforce granular share policies for individual files or folders based upon its contents and context. Files can be deleted, quarantined, or encrypted before they become security incidents.

Choose which types of activity to monitor, such as PII or PHI. Select which action to take, whether it's blocking the email entirely or encrypting it for an authorized user. See all matches and activities on the Check Point dashboard.

-Bijender Mishra
Chief Information Security Officer,
Alkem Laboratories

