Starting Today: Stop shaking hands. Stop clicking on any email that mentions Coronavirus!
Our security analysts have seen a significant rise in phishing emails that try to leverage the COVID-19 pandemic. Taking advantage of the latest crisis, hackers are using the fear and urgency of COVID-19 in order to launch a new round of attacks.
You have been getting emails from your office, your friends, airlines, banks, government agencies and nonprofits, telling you the latest about the outbreak. This has helpSome of them are from people only pretending to be one of them. This helps hackers launch new attacks around the pandemic.
The rise in CoronaPhishing has grown with the rise in our Google searches the virus starting almost the very same day. Attackers use the same search engine optimization tools that marketers use to get you to open an email.
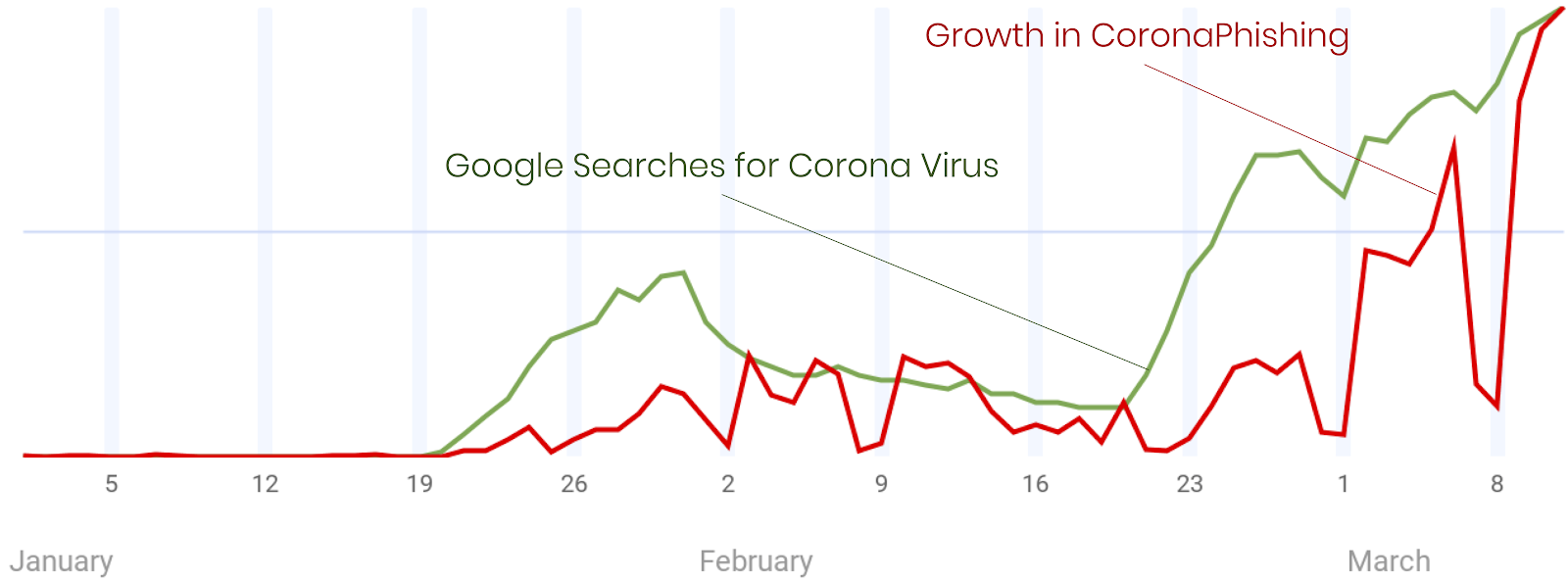
Dips in CoronaPhishing occur when the attackers take the weekend off.
Two common themes of CoronaPhishing campaigns are:
- Fear and urgency: the most effective phishing method to convince people to click a link.
- The latest news: everyone is hungry for updates about the crisis.
With subjects like these, taken from actual campaigns, your hand might instinctively click on a link before your brain has time to stop it.
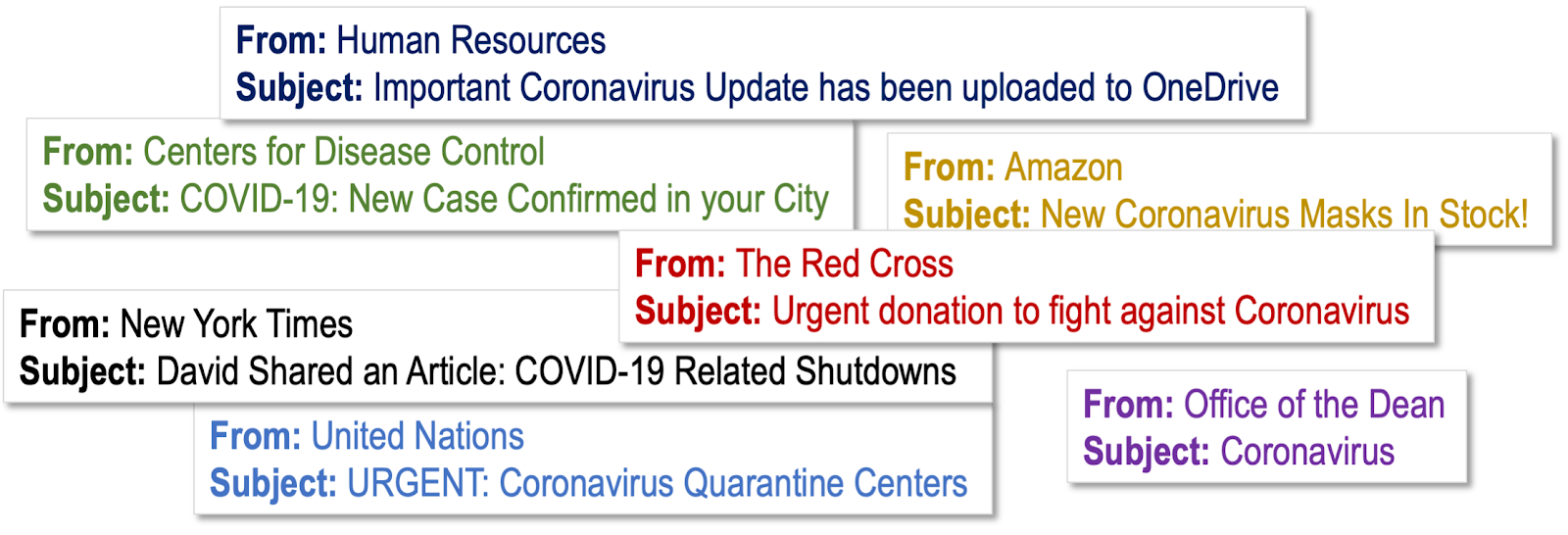
Your end-users should treat every email that mentions Coronavirus COVID-19 with suspicion.
Hackers are leveraging the fact that organizations have been sending out action plans and contingency updates all month. Users expect to seen an email like this:
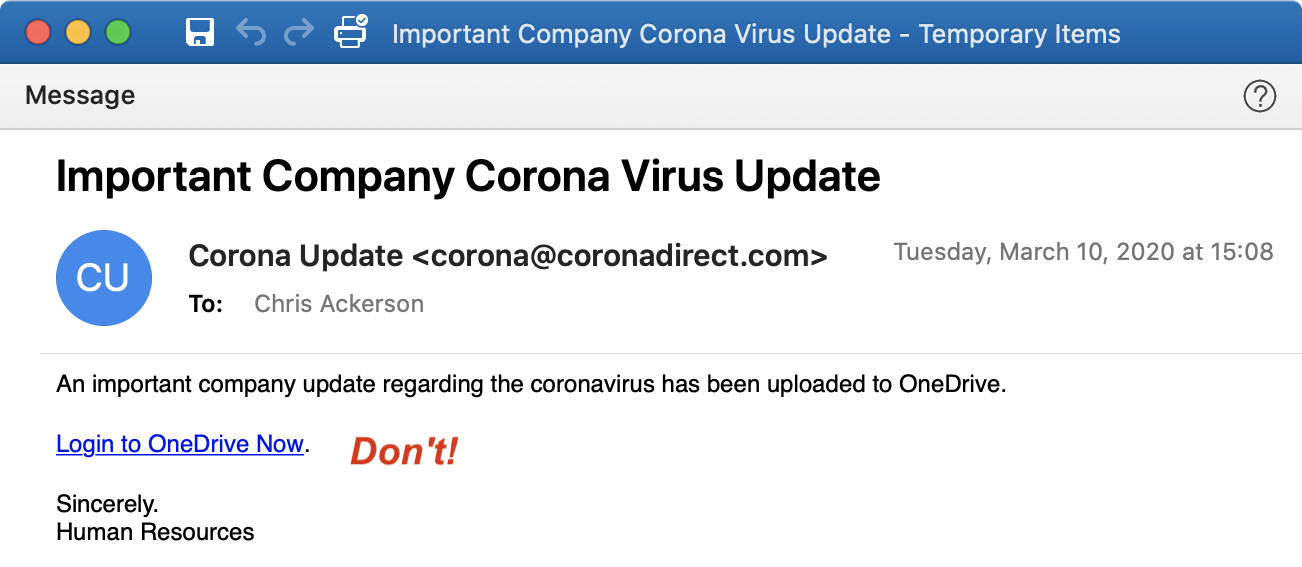
Attackers are not deploying new technologies, but using tried and tested techniques to reach the inbox because it has been a long time since they’ve had such a compelling message. Malicious URLs, malware attachments, password harvesters, auto-redirects and Business Email Compromise attacks are wrapping themselves in a cloak of authority, friendship or insider knowledge to garner a click.
Some are targeting top executives who might be in the middle of an urgent material decision about office closures, travel bans or conference cancelations. A timely and relevant message from the right impostor can be tempting.
Below is an example of another attack, which sometimes even included the recipient's city, indicating a more targeted campaign. The message looked like it was from the CDC and the URL looked like it went to the CDC site, but neither were true.
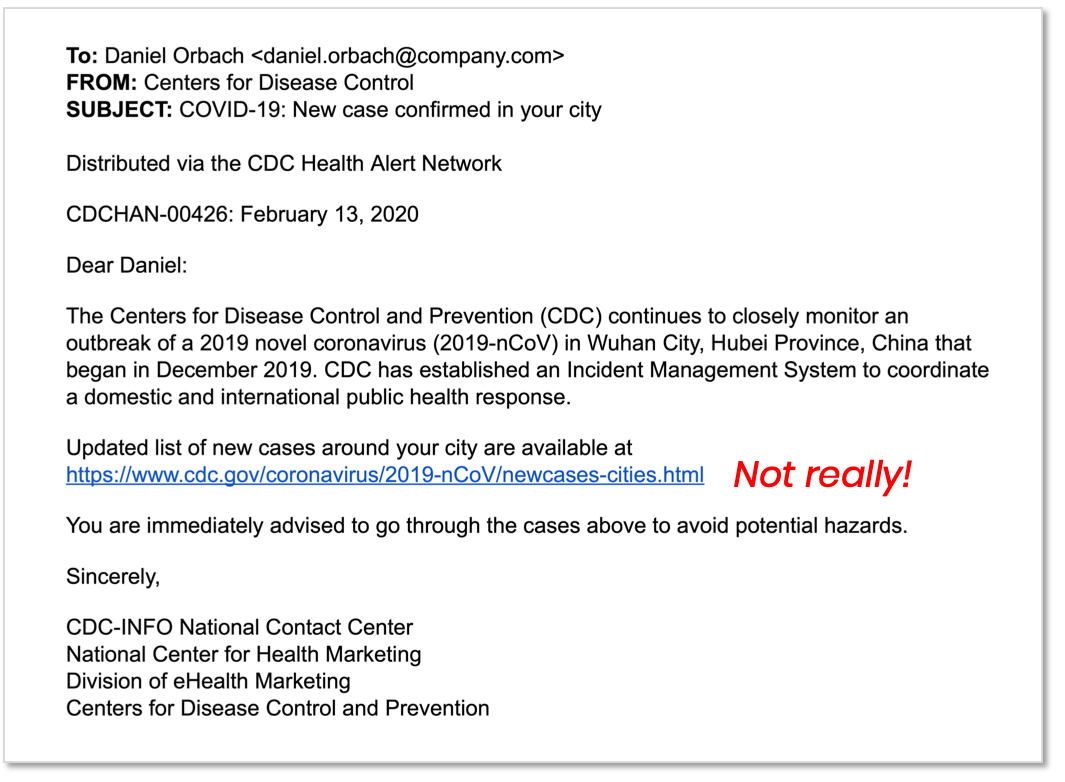
With the healthcare crisis and the economic turmoil, good inbox hygiene is probably the last thing on people’s mind. The attackers know this. They have not stopped working! Even though they, too, are probably working from home.
If you want the latest news about world events, trust Google, not your inbox. And don’t worry, you can still find cat videos there, too.