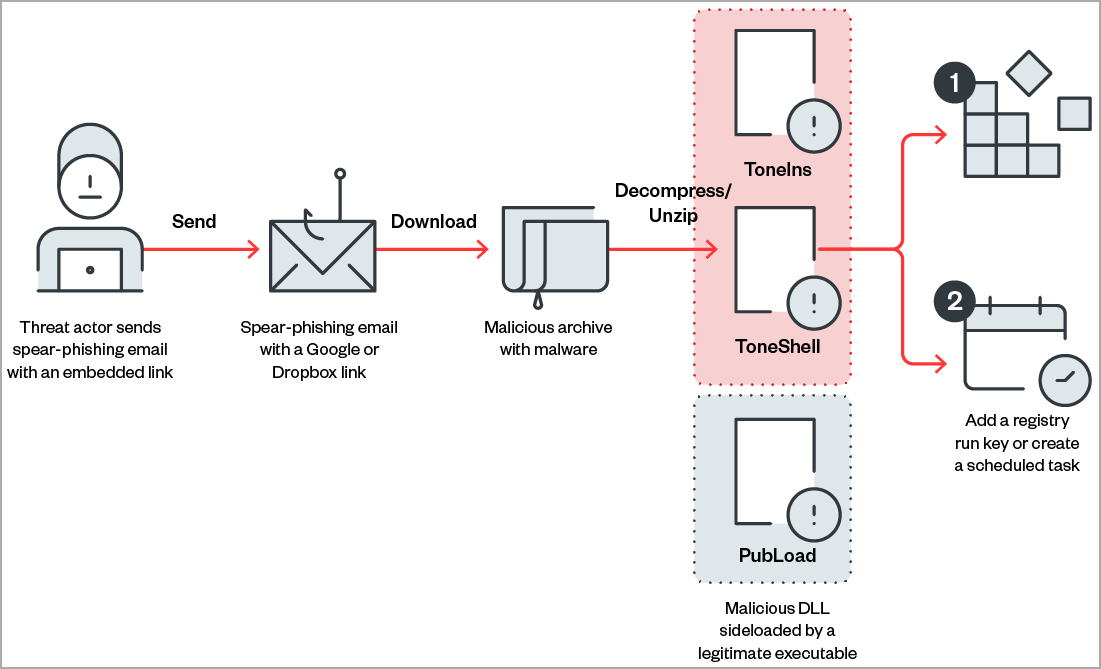
Researchers have uncovered a state-sponsored hacking campaign that uses Google accounts to send emails, and then uses a Google Drive or Dropbox folder as the mechanism for downloading.
The links within the email go to a Google Drive folder, leveraging The Static Expressway to fool security services.
Here, according to Bleeping Computer, is how it works:
The files are unzipped upon downloading and then lead to a few different malware options.
This attack showcases the importance of full-suite protection. The email itself links to a Google Drive page. Google Drive, on its own, is a legitimate site, and most security services would see it and think it's good to go.
This is the premise of the Static Expressway, which we continue to see in droves. Hackers take advantage of legitimate services, like Google Drive, Quickbooks, PayPal and more, to host or send phishing links. Security services think it's safe, and thus it avoids detection.
In this attack, most security services would see that it's a Google Drive link and let it go. And this is where full-suite security comes into play. By scanning file-sharing apps, you would see that the file in question is, in fact, malicious.
Only Avanan scans, tests and executes all files using Check Point's Sandblast to ensure there's no malicious content. Beyond that, DLP tools detect leaks of PII and other sensitive data. By leveraging Avanan's advanced Artificial Intelligence, Avanan can also detect compromised attacks, insider threats and insecure configurations.
Malware doesn't stop at email. It's important to be able to protect against the entire attack thread. In sophisticated campaigns like this one, extending beyond email security to file-sharing security is essential.