This is a large scale phishing attack against Office 365 that we have been seeing across the majority of our Office 365 customers. The attack takes advantage of Office 365's blindness to phishing attacks in which the URL contains special characters.
The attack began on August 2, 2017 and fakes a Dropbox file share email. The link that the hackers use in the email rotates, each time leading to another compromised site; but all the links seem to lead to a fake Dropbox login page. It all looks genuine with one small change - a dot above the 'ȯ'.
The email subject looks like this:
Attached Via Drȯpbox - (Account_liquidation.Pdf)
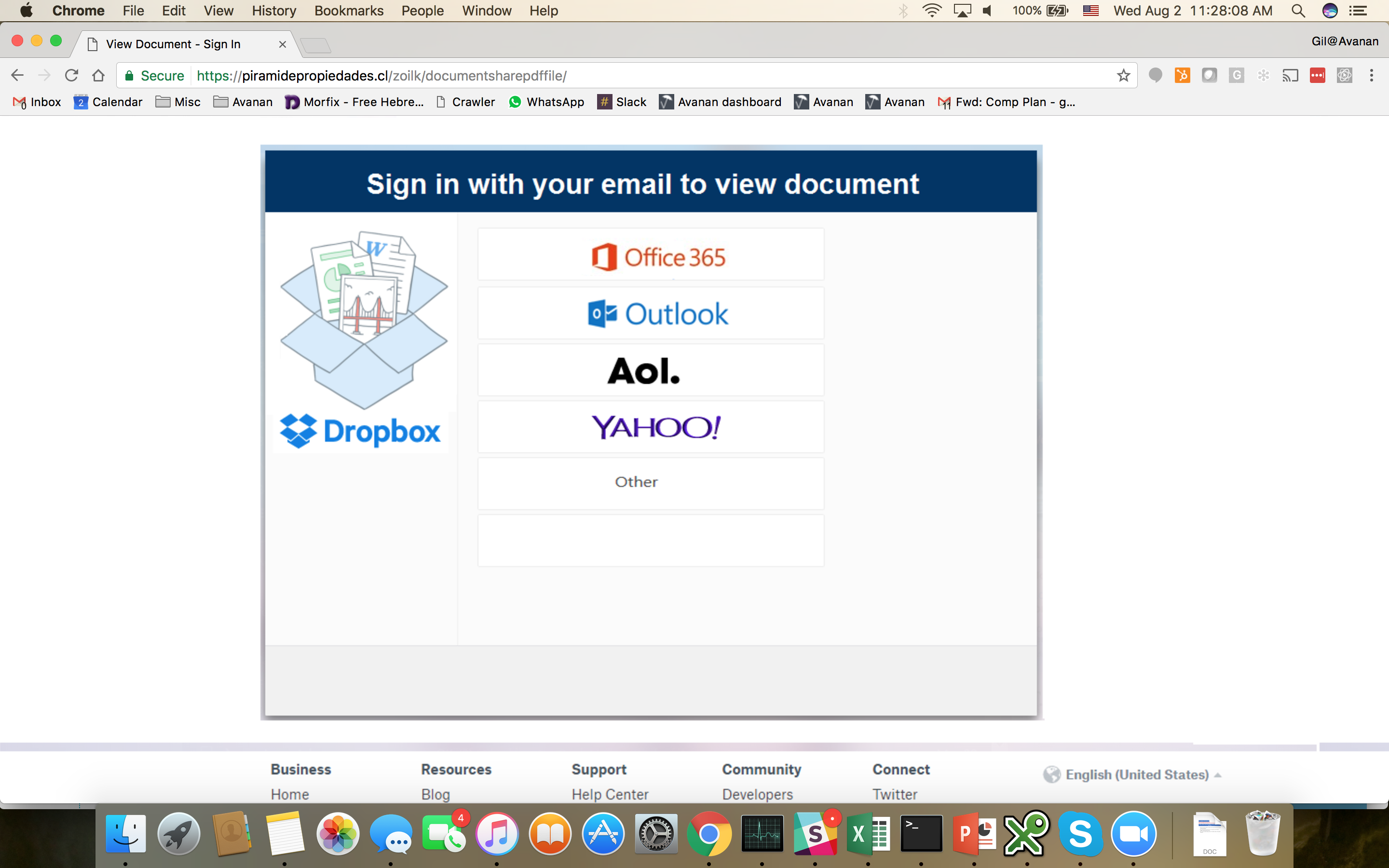
Here's an example of where the link in the email leads to:

The Office 365 service has a notorious history of not detecting phishing attacks when the domain included special characters. For example, in December 2016, we published the punycode vulnerability in the domain name. A similar attack was then reported by other security vendors in March and April 2017.
This new one is yet another variation; the hackers are using special characters in the subject of the email, probably to bypass Microsoft's built in security that looks for known brands like 'Dropbox'.
Please warn your users of this attack. If you want to learn more about how Avanan tracks and blocks these attacks on Office 365 customers, you can reach us at the 'Get a demo' page.
Yoav and The Avanan Team.