We’ve written extensively about phishing attacks that originate directly from QuickBooks. This works by hackers creating accounts directly in QuickBooks and then sending invoices directly from the site to end-users. The catch? There’s malicious instructions, either in the form of a phone number to call or email to engage with.
This is an attack that continues to happen and it’s part of what we call BEC 3.0--using legitimate tools to send phishing attacks.
But phishing comes in all forms and one thing that’s still popular is spoofing attacks. These are attacks that look like they come from a legitimate service, but in fact come from a malicious domain or email address.
We’re seeing an increase in attacks that spoof QuickBooks—hundreds in the last few weeks.
In this attack brief, Check Point Harmony Email researchers will discuss how hackers are spoofing QuickBooks to phish users.
Attack
In this attack, hackers are spoofing QuickBooks in order to try and extract money from end-users.
- Vector: Email
- Type: Impersonation
- Techniques: Social Engineering, Credential Harvesting
- Target: Any end-user
Email Example
This email comes from “Quickbooks Solutions” which is obviously not QuickBooks.
But, if you don’t look at the sender address, you’ll see an email that says your QuickBooks account needs to be upgraded. If you don’t, you’ll lose access to a lot of key services, including payroll, bill paying and more.
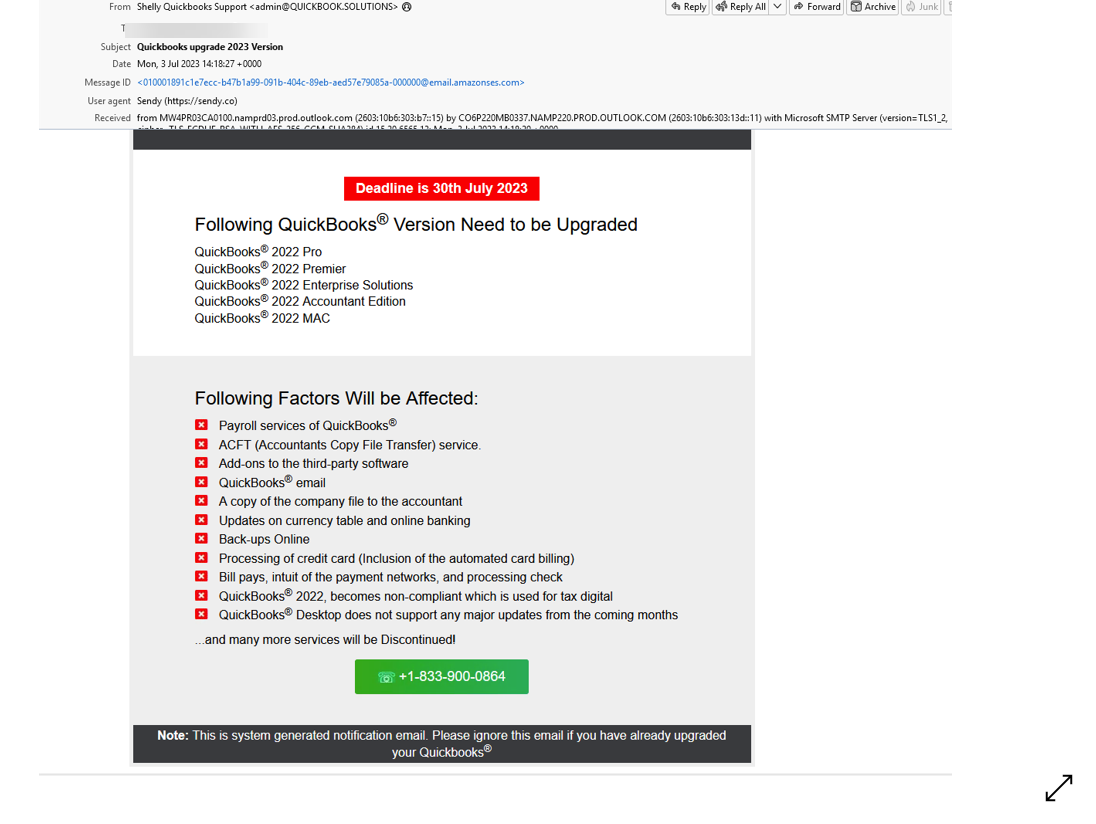
If you work with QuickBooks in your organization, this could be a siren call. You might be willing to give QuickBooks support a call and sort it out.
If you call, though, you’re not going to reach QuickBooks. In fact, it’s a scam number associated with QuickBooks attacks:
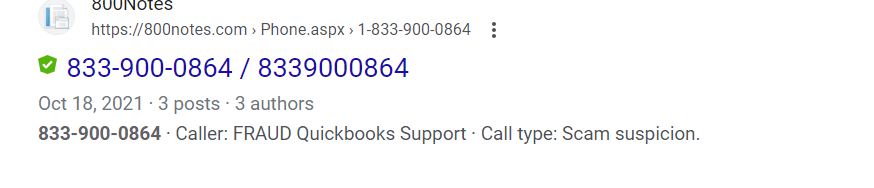
There’s a lot of things that should alert email security services and end-users that something is off. One is the sender's address. It’s not a traditional email address, and it certainly isn’t associated with QuickBooks. Two, the phone number. Our AI scans phone numbers and matches them against scam numbers to see if something is amiss.
Third is the tone. It’s urgent, with lots of red colors. And the grammar is pretty stilted.
All in all, it’s an attack that should raise red flags.
Techniques
Spoofing popular—and even non-popular—brands is an incredibly common phishing tactic. It’s popular because it still works, even if some of the campaigns don’t always look believable.
This attack, which spoofs QuickBooks, is only somewhat convincing. But the attack does a great job of conveying urgency. If you don’t renew, the email says, you will lose access to critical services, such as bill pay, payroll, taxes and more.
If you see that and realize that you may lose access to those tools, you might want to act quickly.
That’s what the hackers are hoping for. All it takes is a moment where the user doesn’t think or act too quickly. That can be all it takes for serious damage can happen.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing, as well as phone numbers
- Implement full-suite security that can also scan documents and file
- Implement robust URL protection that scans and emulates webpages






