Avanan has uncovered a new sextortion attack that uses QR codes instead of URLs to avoid bitcoin wallet detection. To drive the attack, hackers claim they have footage of the victim watching pornography to pressure them into sending ransom funds via bitcoin. Because 98% of emails containing a bitcoin link or crypto wallet address are phishing, most security tools classify any email containing these as suspicious or as instances of phishing. But when hackers use a QR code instead of a link to a bitcoin wallet, Microsoft Office 365 Security (as well as other email security gateways Avanan tested) completely miss the attack.
QR code sextortion attack could reach 10% of Office 365 users
We started seeing this phishing campaign against Office 365 customers on Friday, the 13th of December, through the publication date of this alert. Based on the attacks observed, the initial phishing campaign focused on U.S. municipalities. Over the weekend and early in the following week, the campaign spread to more Avanan customers, including several North American Fortune 500 organizations. Analysis shows this attack affecting about 10% of Avanan customers at the time of writing.
In total, the Avanan antiphishing algorithm stopped several thousand of these phishing emails, indicating that the hackers are attempting to stay under the radar of mass mail detection by selectively choosing victims and avoiding widespread attack. In this case, the sextortion emails included the real password of the victim in its body, indicating that hackers are targeting victims whose credentials have been previously compromised and/or extorted in the past.
How the attack works
This campaign has several key obfuscation features:
- The entire email body is an image.
- The text in the message is obfuscated with special characters to avoid OCR detection.
- Hackers use a QR code instead of the standard link to evade link reputation checking and detection of the bitcoin wallet ID.
- Most attacks were sent from other compromised Office 365 accounts. Their high sender reputation allows the emails to pass SPF.
- Though widespread across the Avanan customer base, the attack is very targeted and avoids any mass-mailer detection by Office 365.

Combined, these obfuscation methods blind Office 365 to the attack. The hackers bypass the default security (EOP), Advanced Threat Protection URL and bitcoin filters, and Safe Links.
How Avanan blocks this attack
Avanan is able to detect these attacks with a QR code analyzer in our OCR engine that identifies the code, retrieves the URL, and tests it against our other engines. The existence of a QR Code in the email message body is itself an indicator of attack. When QR codes point to a crypto-wallet, it receives a maximal phishing score and our algorithm blocks the email before it can reach the end-user.
The Avanan Algorithm
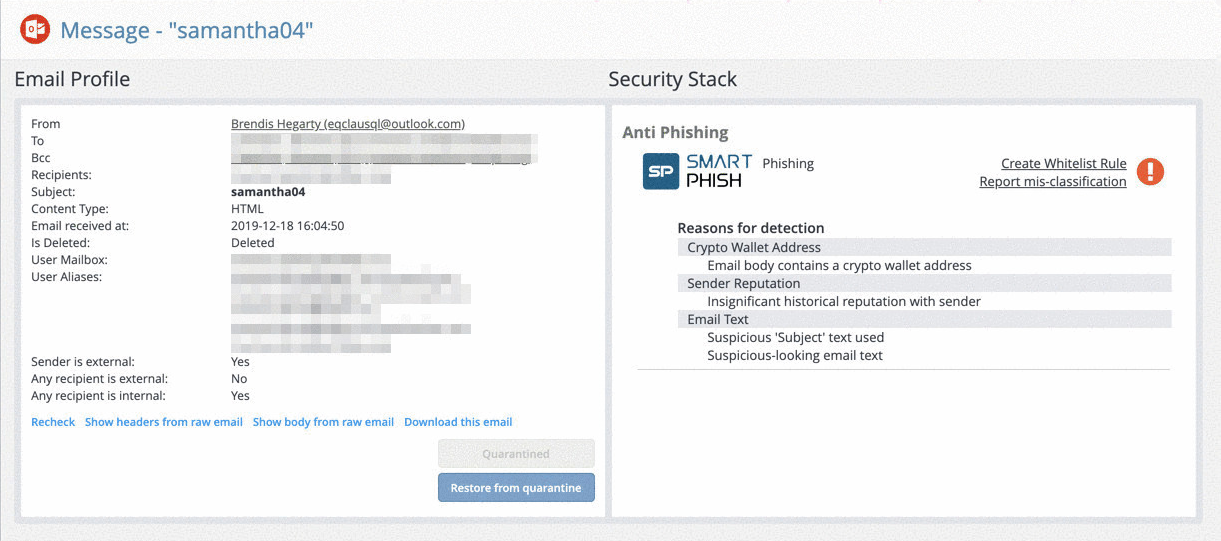
The Avanan Algorithm
- OCR parses the QR code and identifies the link.
- The link analysis layer confirms that the URL points to a crypto wallet.
- The crypto wallet is flagged as a phishing indicator.
- OCR converts the image to text
- Natural Language Processing identifies suspicious language and flags it as a phishing indicator.
Summary
By coding the link in a QR code, this attack demonstrates a new method of URL obfuscation. Avanan predicts that this attack method will continue in future phishing campaigns. Attack analysis suggests that Microsoft security tools don’t scan QR codes, giving hackers an easy way to bypass link-based analysis like Safe Links. (Avanan recently published a blog describing another attack against Safe Links.)
This vulnerability still exists in Office 365, and we are unsure of when Microsoft will address this QR code exploit.
Adding additional layers to cloud provider security is the only way for organizations to protect itself fully against evolving threats. Avanan is uniquely designed to act after Office 365 email security, adding a layer of protection tuned specifically to catch phishing emails missed by Office 365 before they arrive at the end-user inbox, blocking threats before they have an impact.







