In March of 2018, an employee at The Financial Services Information Sharing and Analysis center (FS-ISAC) clicked on a malicious link. From there, the phished email spread in waves throughout the cybersecurity institution, until other employees who received the message reported it to the internal IT director the same day. The FS-ISAC quickly contained and isolated the threat, but not the irony. This incident underscores a key misconception in cloud-based email security: that default email security from Office 365 or Gmail protects against the latest phishing attacks.
Phishing Prevails in 2018
Following the incident in March, the FS-ISAC upgraded their Office 365 to include Microsoft's most advanced threat protection, but made no comment about mandating more security measures. This upgrade is, of course, the quickest fix, but it does nothing to address the underlying problem: built-in email security does not protect against even the most basic types of phishing.
Relying on built-in protections can be a costly decision, with the average payment demanded from a phishing victim at $35,000. Blind spots like this cannot be afforded when:
- phishing and pretexting account for 98% of social incidents and 93% of breaches. Email continues to be the most common attack vector, at 96%. - VDBIR 2018
- a phishing incident at a mid-sized company costs an average of $1.6 million. - Enterprise Phishing Resiliency and Defense Report
- global losses from Business Email Compromise scams will exceed $9 billion in 2018. - Paradigm Shifts: Security Predictions for 2018
And yet, many organizations believe that native Office 365 or Gmail security is complete security. The proliferation of security incidents and account breaches demonstrate that policies, technologies, and procedures have not evolved with the the ever-growing number of attack vectors.
True defense against phishing requires continuous monitoring, complete visibility, and automated responses to keep email safe and dependable.
Layered security stops sophisticated phishing attacks.
Avanan’s policy controls work with your email and users to monitor the cybersecurity health of your organization. Using layers of anti-phishing tools that sit behind your cloud email's default security, Avanan connects directly via API and is specifically designed to catch the advanced phishing attacks that bypass standard email security, such as Microsoft and Google's offerings. We sandbox all incoming files and links to detect known and zero-day threats. On top of this, our machine learning algorithm performs dynamic analysis of email, correlating over 300 phishing indicators in every message.
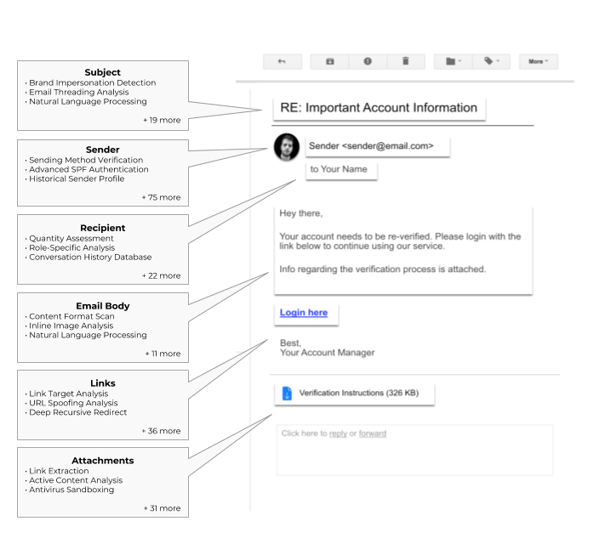
Email breakdown showing some of Avanan's 300+ anti-phishing indicators.
Avanan provides the essential foundations for email security, such as DMARC, SPF, and IAM. But our protective technology goes further, with customized, machine-learning algorithms that protect your information before, within, and after it leaves your inbox.
Cloud credentials are the crown jewel of phishing attacks.
A single user's password can provide hackers with unfettered access to an entire application, and can be used to gain access to additional accounts and different applications.
To combat this, Avanan uses behavior analytics to understand how your users regularly and safely interact with their email and the rest of their SaaS accounts. User Behavior Analytics build a profile from each user’s total event history to determine a baseline for safe behavior. If a user deviates from this standard, Avanan identifies the account as compromised and takes corrective actions to protect enterprise data. Additionally, event logs ensure that user and data activity are managed and correlated into the ongoing narrative of your organization’s security hygiene.
Domain impersonation is a popular method hackers use to spoof trusted services.
Google Chrome's engineering manager, Adrienne Porter Felt, wants to kill URLs because they're no longer a "good way to convey site identity" and are difficult to read. Until we are all living in a URL-less utopia, the threat of URL impersonation is alive and well. Recently, the widespread PhishPoint attacks relied on domain impersonation to harvest credentials. The bad actors were able to target 10% of the Office 365 population because Microsoft’s security tools only scan inbound email links, assuming that the threat lies outside your domain.
Avanan identifies email that might spoof the domain, images, language, or look-and-feel of corporate messages, especially on-line services. It scans files and email (inbound, outbound, and internal) to look for URLs—even if recursively embedded—and actively follows redirected links to measure domain risk and perform individual page analysis.
 Office 365 email analytics provide a detailed look into phishing attempts.
Office 365 email analytics provide a detailed look into phishing attempts.
User impersonation simultaneously betrays and exploits trust.
More difficult to detect than domain impersonation, user impersonation occurs when a hacker spoofs or even gains access to an employee account and leverages their authority to urgently request credentials or protected information from within the organization. In the worst case, they gain credentials belonging to an IT administrator or corporate executive.
User impersonation succeeds because it is often casual and personable, lowering the victims' guard. Avanan even protects your employees from nickname impersonation by getting to know each user individually, identifying common greetings and typical conversation topics while matching roles and permissions against the company roster.

Avanan's geographic access controls.
Account takeovers lurk silently in the background.
The persistence and invisibility of account takeover is the nightmare of IT teams. On average, Avanan finds at least one compromised account in half of new installs, sometimes discovering breaches from months or years before. Monitoring today's email and yesterday's event log is not enough.
Avanan monitors and analyzes all user activity from the first login and continues to monitor all activity across every cloud application, including those authorized by the user that continue when they are offline. Because it is deploys within the SaaS, it can look through historical events and email boxes, even if the breach happened long ago—even if the compromised account has since been closed. It can analyze historical messages, permission events, configuration changes, and behavior anomalies to look for signs of a breached account that may or may not be in use today.
Corrupted files masquerade as legitimate business documents.
Google Docs and SharePoint impersonations make phishing scams even more convincing. Attackers spoof the standard message that users receive when another person in their network has shared a document with them. Worse, they might post a malicious file and share it with a legitimate sharing link, even sending a SaaS-generated sharing email. These impersonations are so detailed that they even replicate the "Open in Docs" button.
Through a self-teaching AI-powered algorithm, Avanan will quarantine files before they can be shared, long before the first potential victim can click on the URL.

A look inside the Avanan quarantine feature.
Easy One Click Security
In one click, you can protect your organization from phishing and impersonation attacks with a valid and complete solution that provides not just visibility, but also automated protection from phishing, all from a single dashboard. Our comprehensive Incident response platform provides defense in depth against phishing and zero-day threats, with remediation on the fly. Avanan's breadth of anti-phishing tools consider people and processes to give you the most thorough email security imaginable.

A glimpse inside the Avanan security events dashboard.