A new survey found that threat intelligence is a critical part of an organization's cybersecurity strategy.
The study, conducted by CyberRiskAlliance, found that three intelligence played a key role in protecting data and reputation. As one respondent said, "without threat intelligence, we would be chasing ghosts."
Some more key findings from the study:
- 62% said that a fear of ransomware attacks was the driver of implementing threat intelligence in their organization
- A majority said that having access to early intelligence is a "core requirement"
- 75% use threat data for malware analysis
Threat intelligence is only as good as the data that feeds it. Limited data will produce limited threat intelligence.
Avanan's AI is powered by ThreatCloud, the world's most extensive cyber threat intelligence database and extends well beyond email threat data to include threat data from millions of devices including mobile, network, endpoint, and cloud.
Compare the difference in threat intelligence datasets below:
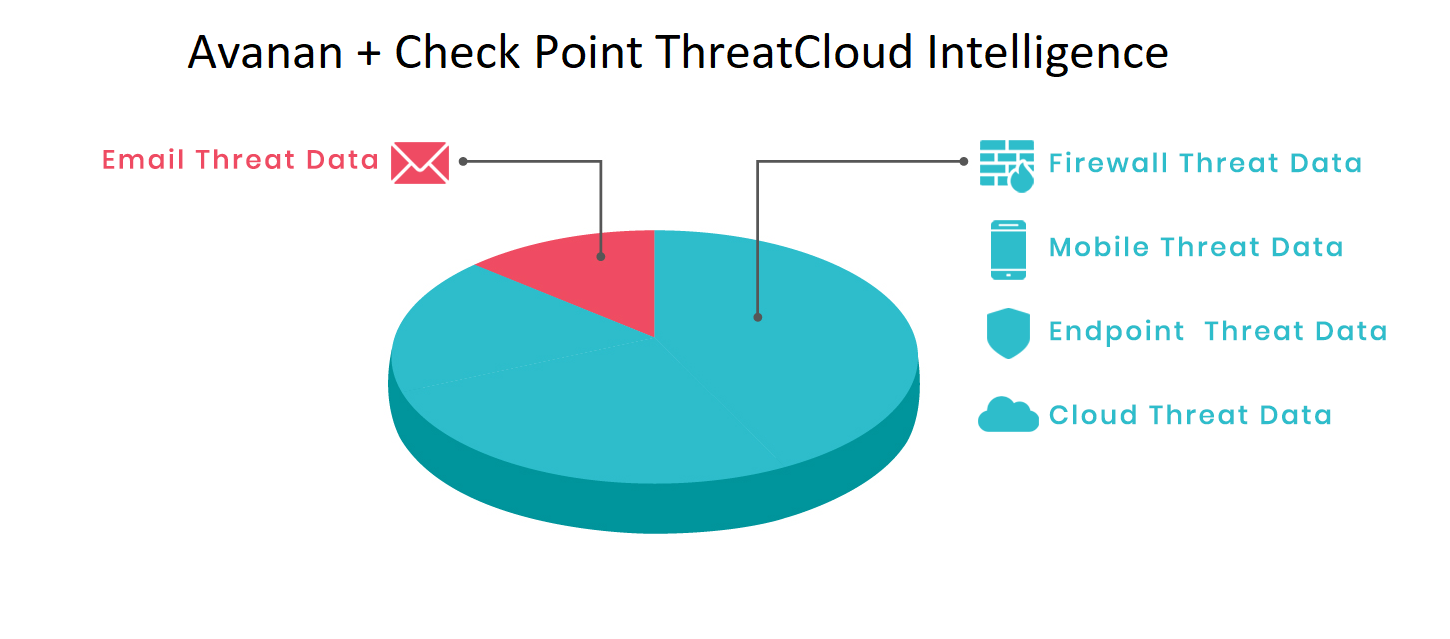

To put the magnitude of Check Point's ThreatCloud intelligence into perspective:
- 150,000 connected networks - Number of connected networks reporting into Check Point's ThreatCloud with millions of endpoints worldwide
- 12 Device Types - Number of device types reporting into ThreatCloud including endpoint, mobile, network device, cloud, and email
- 86 billion - Number of transactions processed by ThreatCloud per day
- 7,000 detections of zero day threats detected each day
- 650K suspicious websites detected per day
- 6.8 Billion malicious website connections blocked last year
- 185 Million malware downloads blocked last year
- 778 Million vulnerability exploit attempts last year
- 200+ of the world’s renowned threat research team - full time threat researchers discovering some of the most significant unknown software vulnerabilities
- 30+ AI Technologies under one single product
Essentially, Avanan's dataset is the most comprehensive on the market. Meaning the threat intelligence is the most comprehensive on the market.
Incorporating this type of threat intelligence will pay massive dividends for security leaders. It is richer and provides more actionable data than a data set just focused on email.
The threat landscape is simply too dangerous to leave things to a narrow set of data. Your organization needs unparalleled access to the best and most sophisticated data.
There's really only one way to do that.






