Recently, we have been seeing a number of phishing attacks using a simple strategy to get their blatant email spoofs past Microsoft's phishing scans. The font manipulation tactic, which we are calling ZeroFont, involves inserting hidden words with a font size of zero that is invisible to the recipient. This is a very old technique, seldom seen anymore, that was once used to bypass spam filters. What makes this attack interesting is that it is now being used to fool Microsoft's natural language processing.

What is natural language processing?
Phishing emails (especially Business Email Compromise attacks) use social engineering and fraudulent text to convince their targets to click a link, enter credentials, or perform some other insecure behavior. In order to block these types of attacks, Microsoft uses natural language processing to scan the content of emails for signs of impersonation or fraud. For example, if the email includes the text "© 2018 Apple Corporation. All rights reserved" in the footer, but the email is not from apple.com, it would be flagged as fraudulent. It uses natural language processing to try to interpret the context or intent of the text and correlate it with the sender. Emails that prompt for things like banking information, user accounts, password resets, and financial requests are scrutinized for authenticity. As Microsoft's filters have become better at reading emails, the attackers are finding ways to fool the language analyzers before they fool the end user. In the ZeroFont method, they have found a way to display different text to the Microsoft filters than what is seen by the end user.
The ZeroFont email
There are multiple examples of the ZeroFont method, but here's a typical scenario.
An email is sent to a customer attempting to impersonate an Office 365 quota limit notification. The message looks like a common administrative service message phishing attack that would normally be caught, but, in this case, it was not flagged by Microsoft as a phishing email. The following image shows what was displayed to the recipient:

The ZeroFont tactic
This email was not flagged by Microsoft is because the hacker inserted random text throughout the email to break up the text strings that would trigger Microsoft's natural language processing. In some cases, random words are used. These inserted characters are embedded within the HTML code <span style="FONT-SIZE: 0px"> to have a font size of zero, making them invisible to the recipient of the email. Below is a screenshot of the raw HTML of the email content, showing the inserted ZeroFont characters.
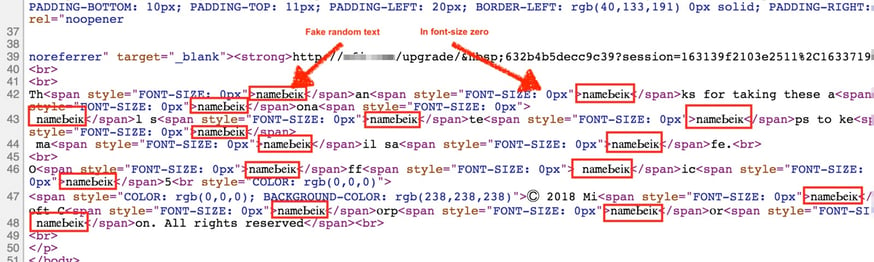
When the recipient reads the email, all the text with "FONT-SIZE: 0px" disappears, leaving the text the attacker wants her to see. The HTML above looks like this to the user:

On the other hand, because Microsoft's filters read the plain text, regardless of font size, they see a seemingly random string of characters:

Microsoft can not identify this as a spoofing email because it cannot see the word "Microsoft" in the un-emulated version. Essentially, the ZeroFont attack makes it possible to display one message to the anti-phishing filters and another to the end user.
You can see for yourself that what you see and what your anti-phishing filter reads might be completely different.
A Convincing BEC email or phishy text hides within a tot a lly different context . An advanced filter or AI scanner should see what you do. If not, your phishing filter would misread the way you see it.
Natural language processing is a vital and powerful tool in the prevention of email phishing attacks. The ZeroFont method is just one way that attackers use to present one email to the security filters and another to the user. Other attacks use different methods with similar results. For example, the Punycode phishing attack, the Unicode phishing attack, and the Hexadecimal Escape Characters phishing attack.









