Recently, we've seen a large rise in QR-code, or Quishing, attacks. These QR codes are delivered via email and contain a link to a malicious credential harvesting page. In fact, we've seen a 587% increase in QR code attacks from August to September.
Many vendors are just coming to market with QR code phishing prevention. We've been doing this for four years. So instead of trying to get our QR code phishing protection up and running, we're innovating and extending the capabilities.
We now have enhanced link re-writing to replace QR codes with new ones that point to a re-written link.
We already utilize link re-writing for all URLs, inspecting them via URL Emulation and ThreatCloud. We also have link re-writing in email attachments, so that links in files are also re-written and inspected.
Now, we extend that to QR codes. We replace the QR code image in the email body with a different QR code, pointing to a rewritten link.
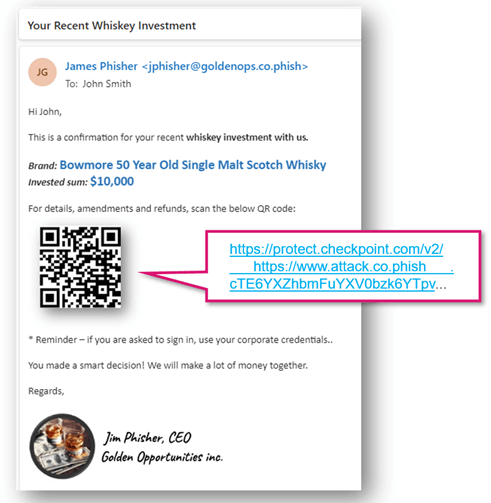
This is critical, especially when it comes to complex phishing attacks that include delayed poisoning of websites, where the malicious part of the website is added by the attacker only after the email is sent.
QR code phishing isn't going away. As vendors scramble to combat the latest threats, we're able to stay ahead of the game.






