Our research has revealed that credential harvesting remains the top attack vector, responsible for 59% of attacks. This malicious tactic also plays a significant role in Business Email Compromise (BEC), accounting for 15% of attacks. Cybercriminals utilize phishing emails containing malicious URLs or attachments to steal and harvest user credentials.
Shockingly, over 50% of these attachments are HTML files that masquerade as login pages of well-known services like Microsoft and Webmail, tricking users into divulging their sensitive information. Our telemetry at Check Point indicates that this is a common tactic used by attackers.
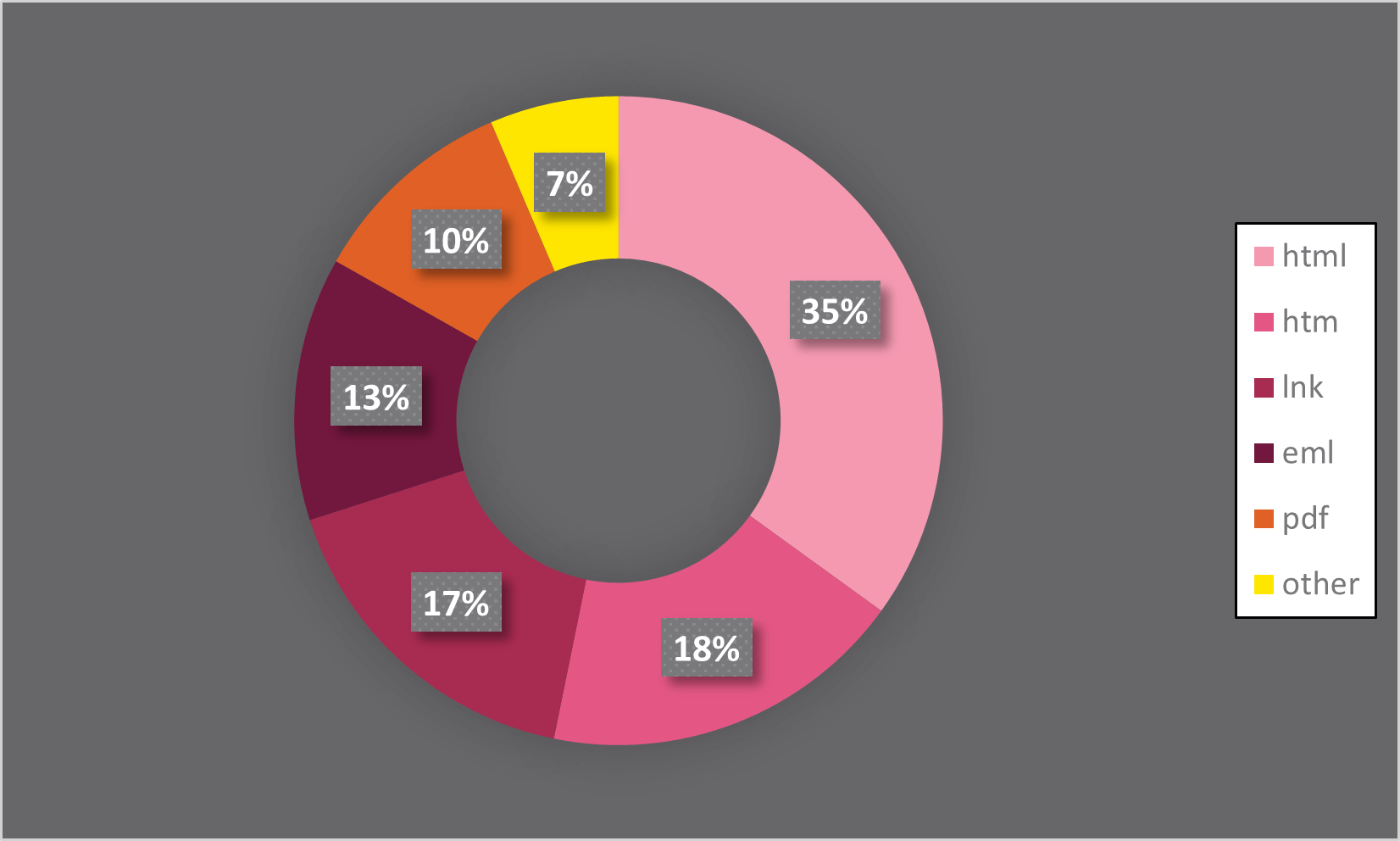
Although HTML is a common part of our daily internet experience, it's important to note that receiving HTML attachments in emails is not the norm for the average person. Unless you work in UX development or design, it's unlikely that you should expect to encounter these types of attachments in your inbox.
If you have recently received an email carrying an HTML attachment, it's increasingly likely that it's a phishing attack. These attachments host web pages on the victim's device, not on the public internet, which is a shrewd way for attackers to avoid URL reputation checks. Malicious HTML attachments in these attacks are equipped with links, JavaScript, embedded images, HTML entities, and customized CSS to escape detection. Some attacks also use advanced obfuscation techniques, similar to those found in the baseStriker and ZeroFont attacks. This attack is especially dangerous in collaboration suites such as Office 365.
By not using a URL, cybercriminals are able to avoid having their phishing page flagged for suspicious activity. This is made even easier by the fact that they can bypass the strict HTML restrictions in email bodies. With no need to host the page on a compromised site, hackers are able to execute these attacks with ease.
To protect against these types of attacks, security experts should exercise caution when encountering emails with HTML or .htm attachments. Additionally, administrators may want to consider blocking HTML attachments and treating them similarly to executable files such as .exe or .cab. By taking these measures, organizations can significantly reduce their susceptibility to credential harvesting and Business Email Compromise attacks.






