MICROSOFT 365 ANTI-PHISHING FOR MICROSOFT 365
MICROSOFT 365 ANTI-PHISHING FOR MICROSOFT 365
Phishing has changed because email has changed. Built-in security in Microsoft 365 isn’t doing enough to stop targeted phishing attacks like Business Email Compromise (BEC), that blend pin-hole vulnerabilities and social engineering to deceive and manipulate end-users. BEC is perhaps the strongest example of how Microsoft Exchange Online Protection (EOP) and even Advanced Threat Protection (ATP) fail to thwart sophisticated hacker methods.
Check Point deploys between the inbox and Microsoft’s native security for Microsoft 365. It secures inbound, outbound, and internal email from phishing attacks that evade Advanced Threat Protection and Secure Email Gateways. It works with these other solutions and doesn’t require any MX record changes that broadcast security protocols to hackers.
Artificial Intelligence (AI) and Indicators of Compromise (IoCs) used in the past train the Avanan platform for what to look for in complex zero-day phishing attacks. Avanan is designed to replace point solutions to deliver a comprehensive solution for all types of phishing — even vector-less attacks.
Check Point connects in a cloud-native manner, no proxy or agent. Its patented API-enabled, in-line security provides many advantages over conventional solutions — such as Secure Email Gateways (SEGs) or Advanced Threat Protection.
With Check Point, Security Operations and IT professionals can more easily investigate, detect, and respond to email-based threats. Using sandbox detonation, zero-day protection, anti-spoofing technology, and URL scanning, the AI inspects every part of the email to uncover threats that others miss.
These continual monitoring capabilities help security professionals in Microsoft 365 understand the state of the inbox, user, and organization.
Legacy solutions designed when on-premises email was the standard are ill-suited to the cloud. As with any technological shift, the transition was complicated. This resulted in an awkward end-user and administrator experience for Microsoft 365 customers opting for third party security, like secure email gateways.
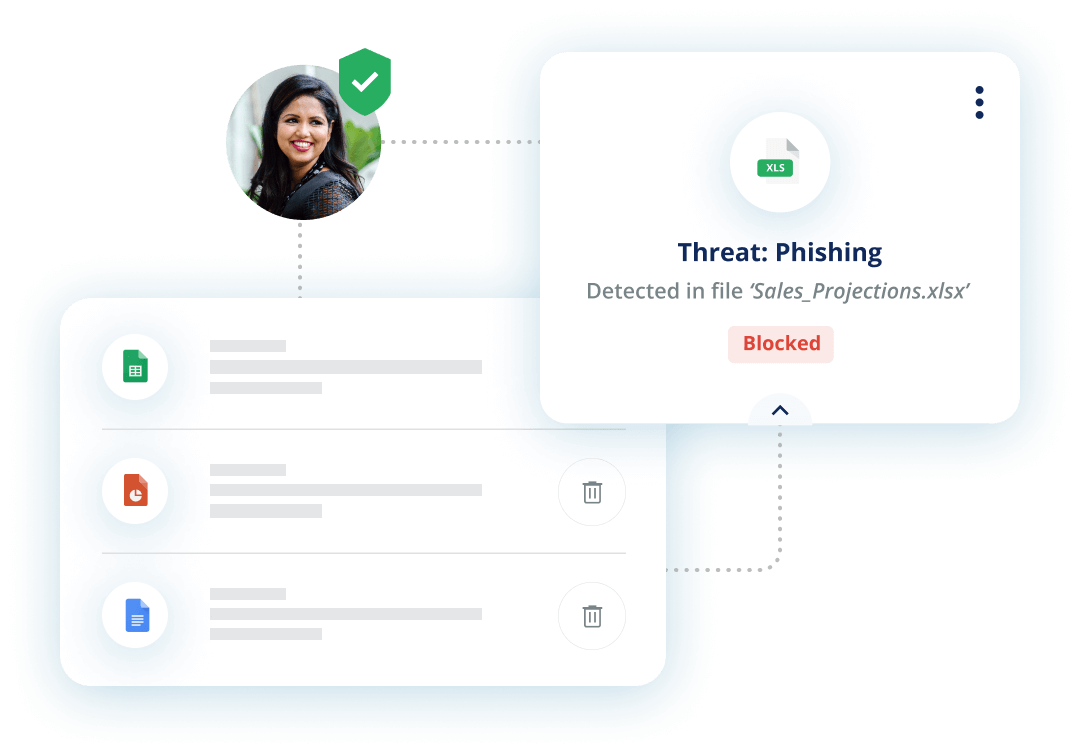
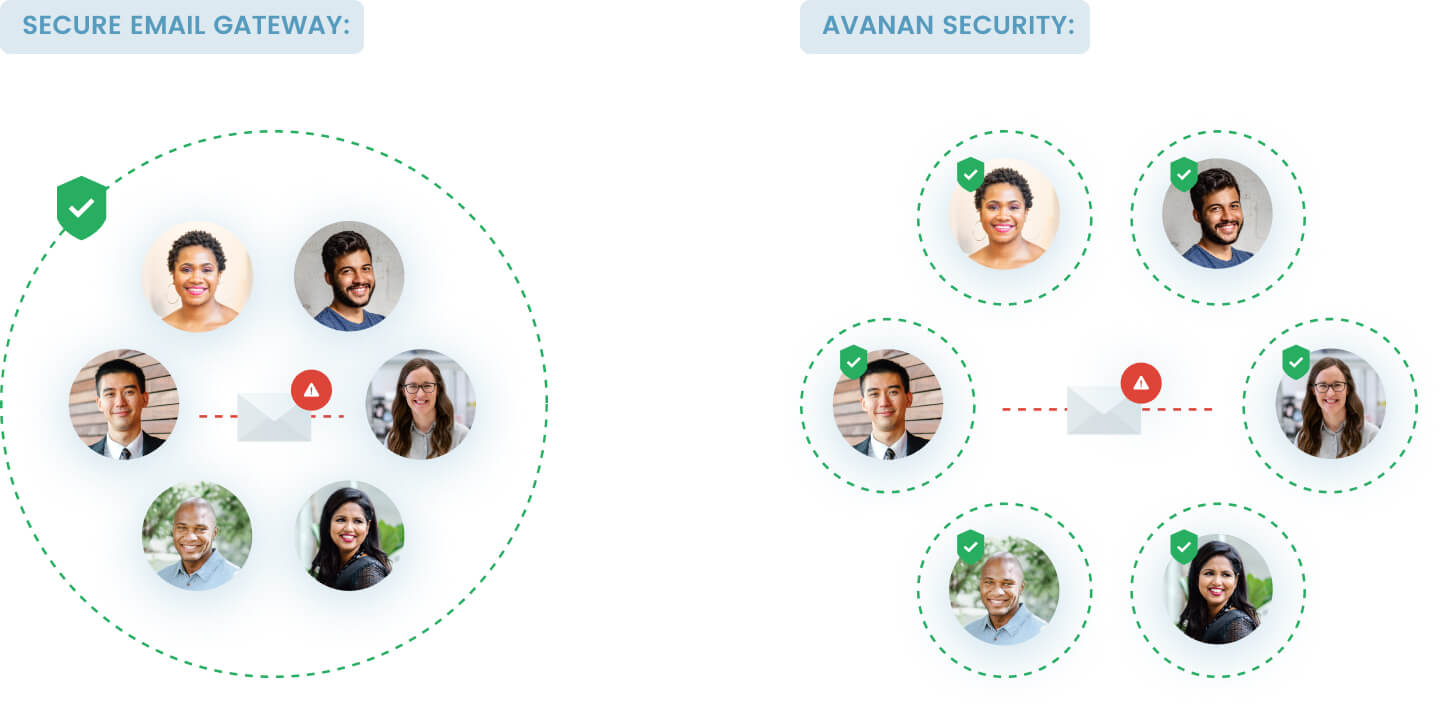
SEGs, or Mail Transfer Agents (MTAs) as they were called, sit outside the cloud, scanning incoming emails. This is useful for inbound attacks but falls short for filtering and blocking internal emails. These are the source of many sophisticated phishing attacks that stem from account compromise and insider threats to the organization.
Check Point secures each individual Microsoft 365 inbox, protecting against phishing attacks from external as well as internal emails. With this strategy, Avanan takes a modern approach to email security. Moving beyond the perimeter-based philosophy of security that was established in the 1990s, Avanan leverages identity to secure the entire environment beyond just the perimeter.
Microsoft has gone to great lengths to develop their anti-phishing and anti-malware offerings, from the standard protection of EOP to the advanced, multi-layer security available in ATP. And yet, hackers consistently innovate methods designed to bypass both security solutions.
Nearly three-quarters of all corporate users experience at least one compromised account per month.
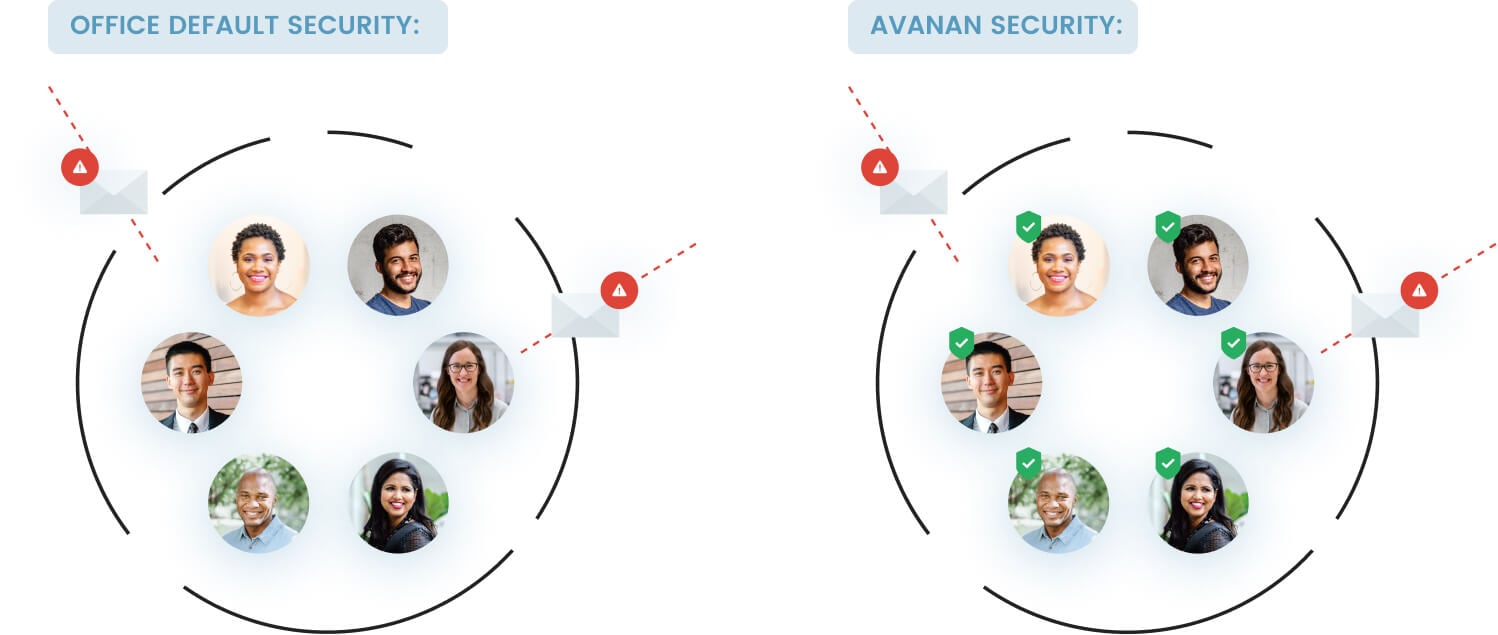
Because Microsoft 365 is deployed at thousands of organizations, many of them large Fortune 100 companies, they cannot afford false-positive detections. If important emails are being consistently quarantined, the disruption to the business — and loss of profits — would be intolerable. Knowing this, Microsoft builds its security to a specific threshold.
Avanan knows this because we integrate with EOP and ATP for Microsoft 365. Our anti-phishing algorithm runs/deploys between these security solutions and the inbox. This enables the AI to train itself specifically on the sophisticated attacks that were designed to evade default security and Microsoft 365 Advanced Threat Protection, without hindering existing security’s ability to filter out spam and low-level phishing attacks.
At the same time, Check Point learns from the cyberattacks missed by other security vendors who also integrate with the Microsoft 365 environment — most notably, secure email gateways and API-based solutions that are similar to Check Point, but lack pre-inbox threat detection. The AI is tuned to what other anti-phishing solutions miss. These unique features combine to give Check Point a threat intelligence database that is unparalleled on the email security market.
Security engineers familiar with Microsoft 365 know that even with ATP’s Threat Intelligence Dashboard, cleaning up post-attack isn’t as easy as it should be. Having to write PowerShell scripts from within a consolidated reporting dashboard with limited drill-down capabilities feels redundant and frustrating.
Check Point customers can manage all their Microsoft 365 anti-phishing requirements for security and compliance from a single dashboard. They can easily set phishing workflows that automate security administration and threat monitoring.
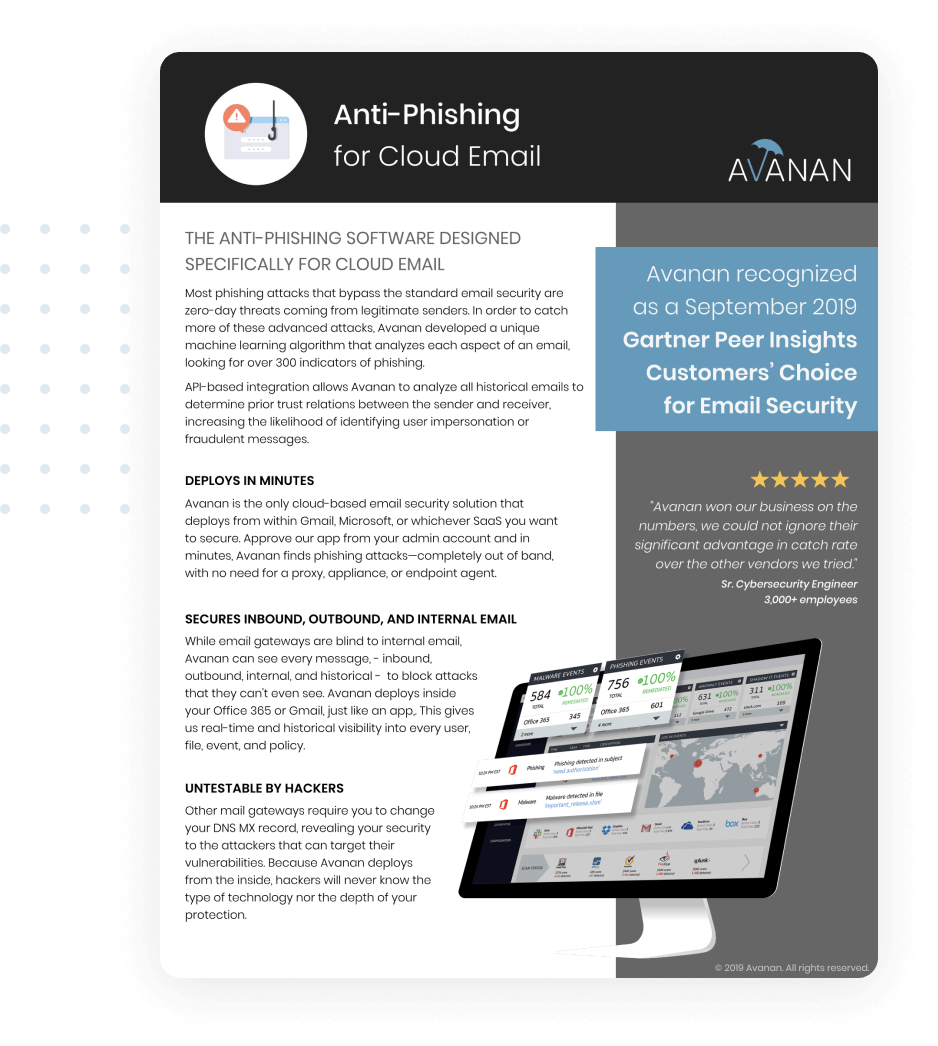
See every threat caught by Check Point, the email subject, content, and why it was determined to be phishing based on the 300+ indicators Check Point looks at in every email. Phishing indicators are explained in plain English, so it’s easy to assess the potential impact of an attack. The simplified view in Mail Explorer allows admin to quarantine advanced threats across inboxes by searching:
With the click of a button, Check Point quarantines all emails that match these parameters to isolate the threat. Using Queries, security engineers in Microsoft 365 can customize the components of their search beyond the options available in Mail Explorer. After identifying advanced persistent threats in the query tool, security professionals can:
The Avanan policy wizard enables the creation of granular policies that apply across Microsoft 365 email to the rest of the collaboration suite. There are three modes of protection available for email.